OnionDSL - Surveillance Frustrating Broadband
Offering Tor or VPN services over-the-top of a normal Internet connection is the most common way for people to connect, however misconfigurations and exploits can result in leaked meta data or clear net browsing that can compromise your privacy.
The OnionDSL design however is a closed network between your DSL modem and the Brass Horn Comms Tor bridges which may make the collection of Internet Connection Records (and by extension other forms of bulk surveillance) less effective.
This is achieved by only issuing private IP addresses to remote endpoints which if ‘leaked’ won’t identify you or Brass Horn Communications as your ISP. (Furthermore your computers aren’t technically connected to the Internet so can’t communicate to the servers that the exploits need to connect to in order to leak your address.) and your router / PCs connecting directly to the Tor bridge in order to reach the Internet.
How it works: DSL
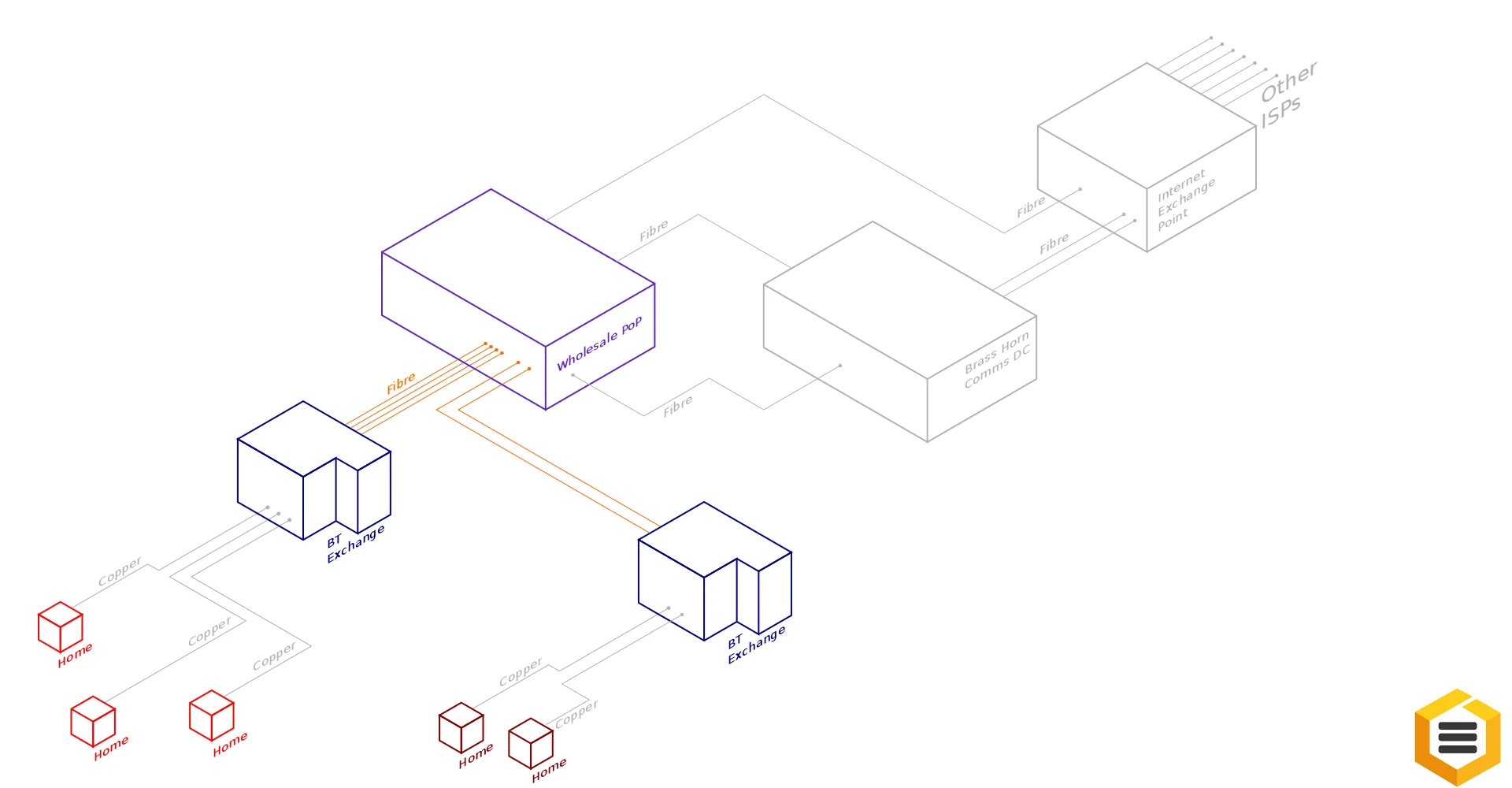 By moving your Broadband / ADSL / FTTC service to Brass Horn Comms your modem will pass traffic via an L2TP tunnel across a wholesale providers infrastructure and terminate within our network.
By moving your Broadband / ADSL / FTTC service to Brass Horn Comms your modem will pass traffic via an L2TP tunnel across a wholesale providers infrastructure and terminate within our network.
How it works: PoP Backhaul
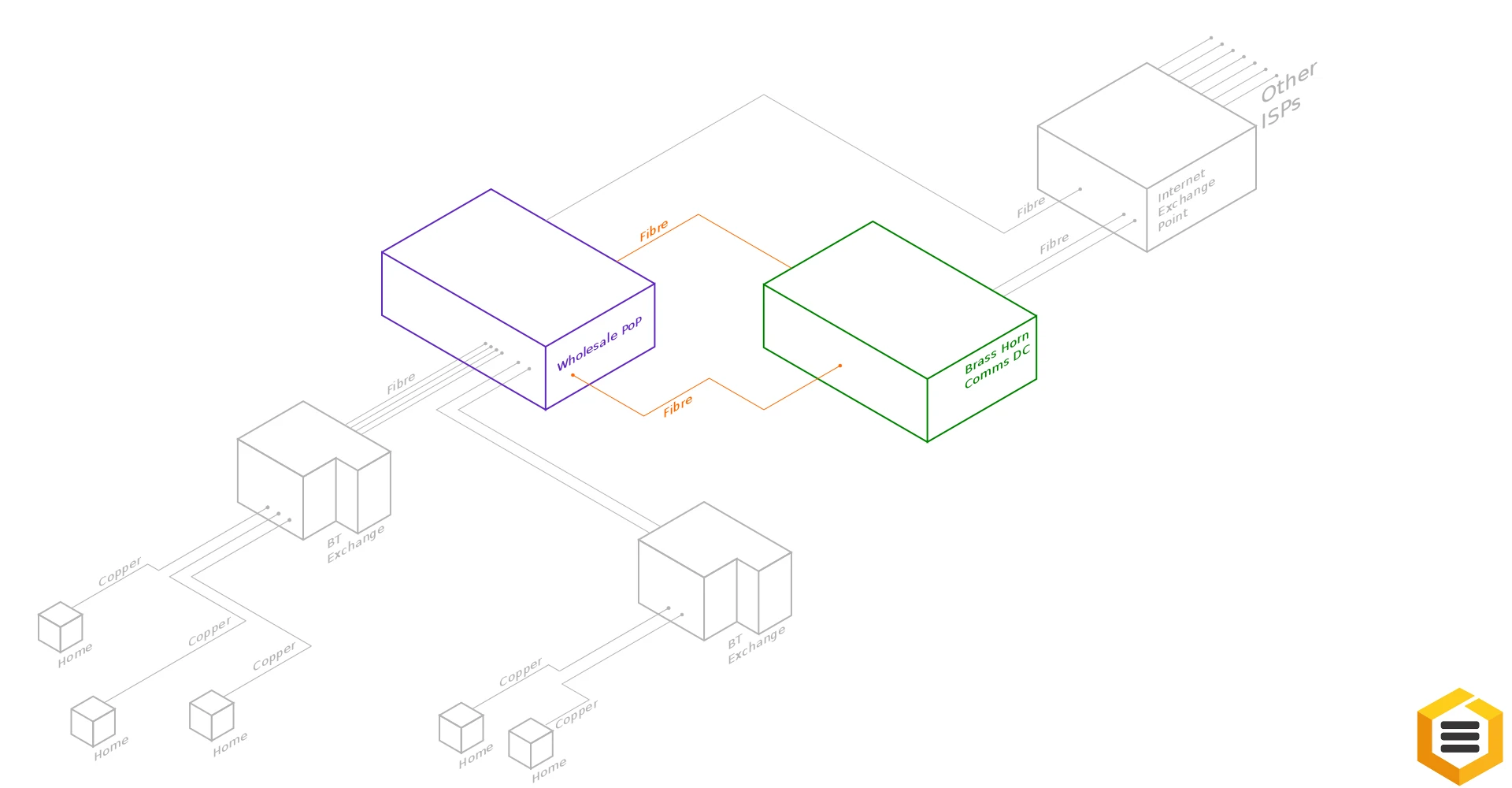 In order for your modems connection to terminate within our network we run fibre optic cables from our datacenter to the Point of Presence of the wholesale provider.
In order for your modems connection to terminate within our network we run fibre optic cables from our datacenter to the Point of Presence of the wholesale provider.
How it works IXPs
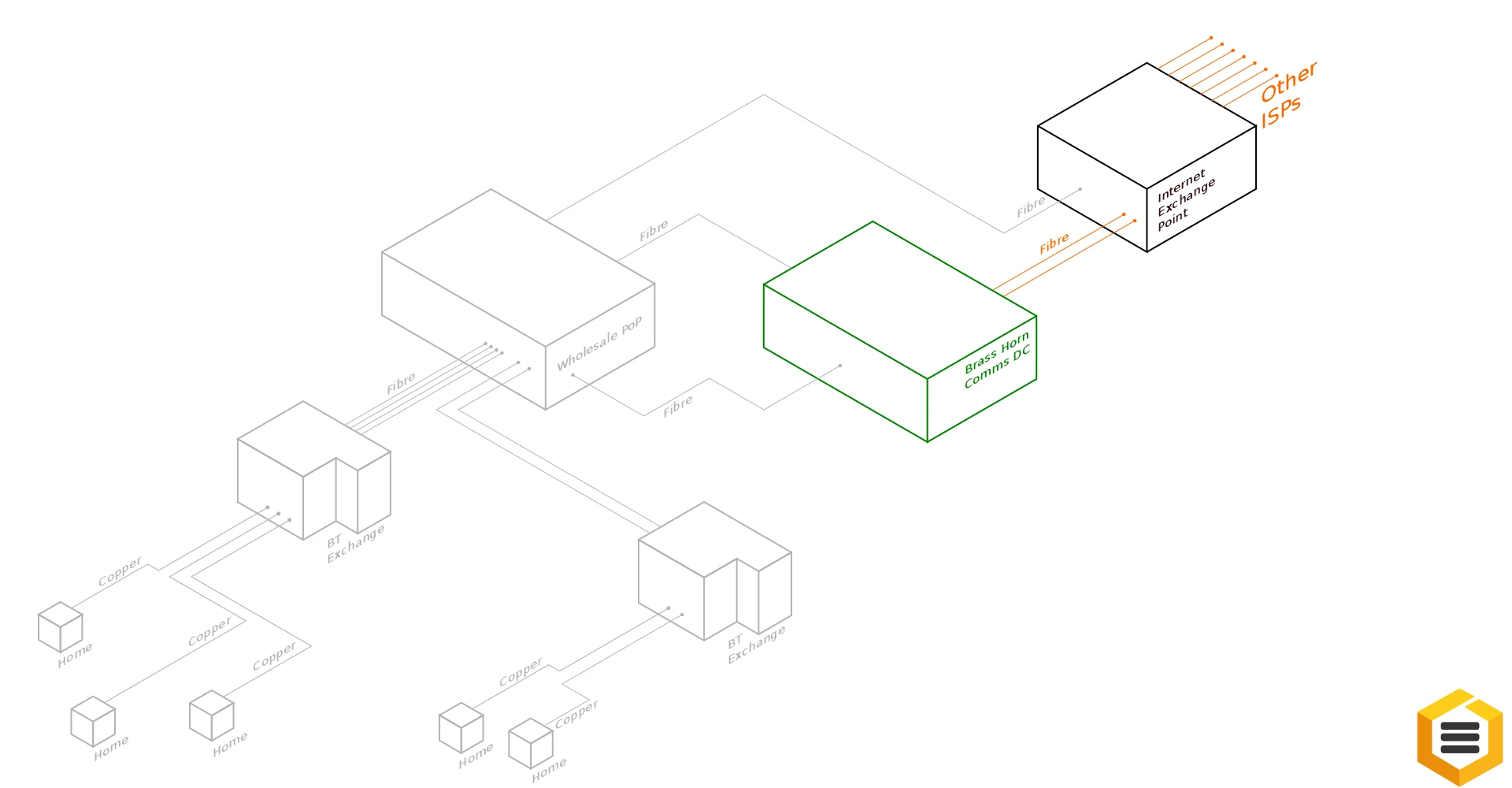 Internet Exchange Points are where ISPs interconnect their routers to pass traffic between each other. By connecting to other ISPs at an IXP we reduce our traffic costs and allow those using our Tor Exits a better grade of connectivity to content networks.
Internet Exchange Points are where ISPs interconnect their routers to pass traffic between each other. By connecting to other ISPs at an IXP we reduce our traffic costs and allow those using our Tor Exits a better grade of connectivity to content networks.
How it works: Bridges
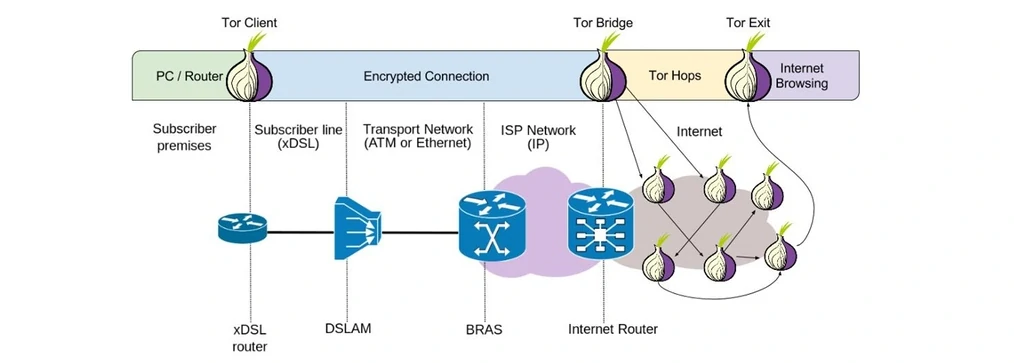 As your modem / computers only have RFC1918 addresses and can only reach the Tor Bridges it is impossible to accidentally ‘leak’ information to the clearnet. After configuring your devices to connect to the Brass Horn Comms Tor bridges you will then have full access to the Internet whilst being protected by Tor.
As your modem / computers only have RFC1918 addresses and can only reach the Tor Bridges it is impossible to accidentally ‘leak’ information to the clearnet. After configuring your devices to connect to the Brass Horn Comms Tor bridges you will then have full access to the Internet whilst being protected by Tor.